How To Use Filters On The Asset Page?
On the Asset Page, utilize filters like status, assessment, and risk score, along with comparison methods such as Equal and Greater Than, for quick and effective management of your cybersecurity assets, ensuring streamlined oversight.
Version Number: v1.0.2
Published Date: 05 Jun 2024
____________________________________________________________________________
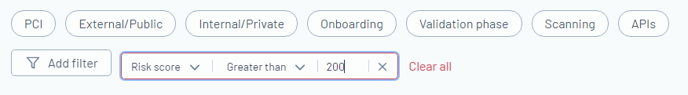
| Filter Purpose | Filter Name | Filter Description |
| Asset Management Filters | ASM Status | Tailor the asset view according to the Asset Security Management status, selecting from Disabled, Blocked, or Scanning, to focus on specific operational states. |
| Asset Status | Drill down into assets based on their lifecycle phase, like Onboarding, Idle, or Staged, to manage assets at different stages effectively. | |
| Asset Tagging | Utilize tags for granular management, filtering assets that are tagged, not tagged, or tagged with specific keywords, enhancing organization and searchability. | |
| Assessment Filters | Assessment Active | Identify assets currently under assessment, enabling real-time tracking of security evaluations. |
| Assessment Status | Sort assets by their assessment phase, such as Automated scanning or Paused, to monitor progress and address needs promptly. | |
| Assessment Type | Filter by the type of assessment, distinguishing between Automated, Penetration Test, or PCI scans, for targeted review of assessment strategies. | |
| Date and License Filters | Created at | Filter assets by critical dates to prioritize actions based on creation, last assessment, or upcoming assessments. |
| Last Assessment Date | ||
| Next Assessment Date | ||
| License Information | Filter by license name, start date, and end date, focusing on compliance and license management. | |
| Security and Compliance Filters | Blocked Status | View assets by their accessibility status, categorizing them as Unblocked, Blocked, or Verifying, to ensure smooth operation and compliance. |
| PCI Enabled | Focus on assets with PCI testing enabled, facilitating compliance with PCI DSS requirements. | |
| Risk Score | Manage risk by filtering assets based on their risk score, highlighting areas of high vulnerability for prioritized attention. | |
| Technical Filters |
Location | Narrow down assets by their physical or digital location (hostnames, URLs, IPs) or by asset name, for specific searches. |
| Name | ||
| Network Access | Differentiate assets based on their network exposure, whether External or Internal, aligning security measures with access levels. | |
| Open Vulnerability Count | Focus on assets by the volume of open vulnerabilities, directing remediation efforts where they are most needed. | |
| Type | Filter assets by their type, such as Network, Web Application, or Container, for specialized management approaches. |
Each section and its associated filters are designed to provide comprehensive control over how assets are displayed and managed, ensuring users can easily navigate and prioritize based on specific criteria. This detailed approach allows for efficient asset oversight, aligning with security, compliance, and operational needs.