How To Navigate The EASM Page In Edgescan?
The EASM Page in Edgescan is your central hub for conducting and reviewing cybersecurity assessments of your organization's external attack surface.
Version Number: v1.0.1
Published Date: 13 May 2024
____________________________________________________________________________
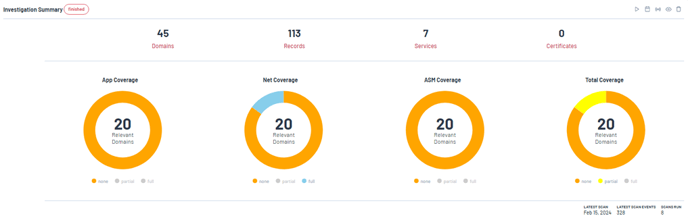
Located at the top of the page is the "Investigations" section, where the latest investigation summary is prominently showcased through informative visuals.
This summary offers a quick overview of key findings, such as:
- Domains Found: Total count of unique domains identified.
- Records Found: Various DNS records revealed during the investigation.
- Services Found: Services detected running across the identified domains.
- Certificates Found: SSL/TLS certificates obtained, indicating secure connections.
Below the investigation summary, circle graphs visually depict the coverage of application, network, and overall attack surface management, including:
- App Coverage: The percentage of applications included in the investigation.
- Net Coverage: Analysis of network elements.
- ASM Coverage: The scope of external attack surface management.
- Total Coverage: An overall view of the investigation coverage.
Actionable Icons
Adjacent to the visuals, action icons facilitate direct engagement with the platform's features, allowing you to (in order):
-
Start a New Scan: Initiate an immediate scan of your external attack surface.
-
Schedule a Scan: Set up future scans at regular intervals.
-
View Investigation Stream: Access real-time updates and activities of ongoing investigations.
-
View Investigation Results: Review detailed findings from completed investigations.
-
Delete Investigation: Remove an investigation from your records
Build your EASM Investigation
Within this section, we will delve into two distinct methods for setting up our EASM (External Attack Surface Management) investigation: the Simple Setup and the Advanced Setup. Opting for the Simple Setup only requires a target domain to kick off the scan, making it a user-friendly choice for those looking for a straightforward process. On the flip side, the Advanced Setup involves more intricate configurations but provides a wider coverage across different task types, catering to users in need of a more thorough analysis.

Setup Tasks
The Investigations page provides a detailed breakdown of tasks involved in the investigation, categorised as either "Required" or "Optional":
| Feature | Feature Description | Requirements |
| Brute-force Subdomain Enumeration | Uses a brute-force approach to guess potential subdomains of target domains | Required |
| Last Registrant Retrieval | Retrieves the last (most recent) registrant of a domain | Required |
| DNS Resolution | Resolves the DNS records of a domain | Required |
| Subdomain discovery | Discovers subdomains of target domains by querying publicly available resources like search engines and social media | Required |
| Domain Registration Exploration | Finds domains that are registered or have been registered in the past by the same entity that registered a target domain | Optional |
| Service Discovery | Discover open ports and running services on discovered domains | Optional |
| HTTP Defensive Header Grading | Grade defensive headers for http and https services. Defensive headers include Content-Security-Policy, X-Content-Type-Options, X-Frame-Options, X-XSS-Protection, and Referrer-Policy | Optional |
| Certificate Retrieval | Retrieves certificates for domains and reports their validity and expiration dates | Optional |
| HTTP(s) Probe | Probe HTTP(s) service availability and status. Note that this is redundant if you are also using the Service Discovery task. It is offered as a lightweight alternative for situations where port scanning would not be appropriate | Optional |
| Typosquatting and Similar Domain Discovery | Reports domains that are lexicographically similar to target domains. This can help identify typosquatting and domains using other TLDs with the same name. Note that this task can take a long time to complete and may generate a lot of noise | Optional |
Regexes
Regex, short for 'Regular Expression', is a tool for matching patterns in text. It acts as a powerful filter for specific string patterns.
While a comprehensive guide to Regex syntax is beyond this manual, we encourage further exploration online. This guide uses the Ruby style of Regex, known for its specific syntax rules. Tools like Rubular, a Ruby regular expression editor, are recommended for testing and ensuring correct syntax.
Example: For the regex 'edgescan', matches include 'http://edgescan.com ' and '123edgescan.com', but not 'edge123scan.com' or 'edge.scan.com'.
Setup Schedule
You can easily schedule scans to fit any timeframe. For example, a monthly scan is set to begin on February 22nd. Our scheduling options are flexible, including daily, weekly, monthly intervals, and more, allowing for customized investigations that meet your specific requirements.

Investigation Stream
The interface of the EASM tool, known as the 'Investigation Stream,' is showcased in the screenshot below. This feature allows users to monitor a stream of results that includes new domains, records, services, and registrants. On the left side, a summary presents key statistics such as 21 domains, 70 records, 3 services, and 0 certificates that have been identified. 
The interface is interactive, offering options to filter the stream by domains, records, services, and registrants. An ongoing scan is indicated in the example, with 193 scan events recorded and 144 registrants discovered. The right side of the interface displays newly found domains and records, showcasing the progress of the active investigation.