How To Navigate The Asset Page On Edgescan?
The Asset Page in Edgescan serves as your centralized hub for a detailed overview and management of your organization's digital estate
Version Number: v1.0.3
Published Date: 4 Nov 2025
____________________________________________________________________________
Main asset page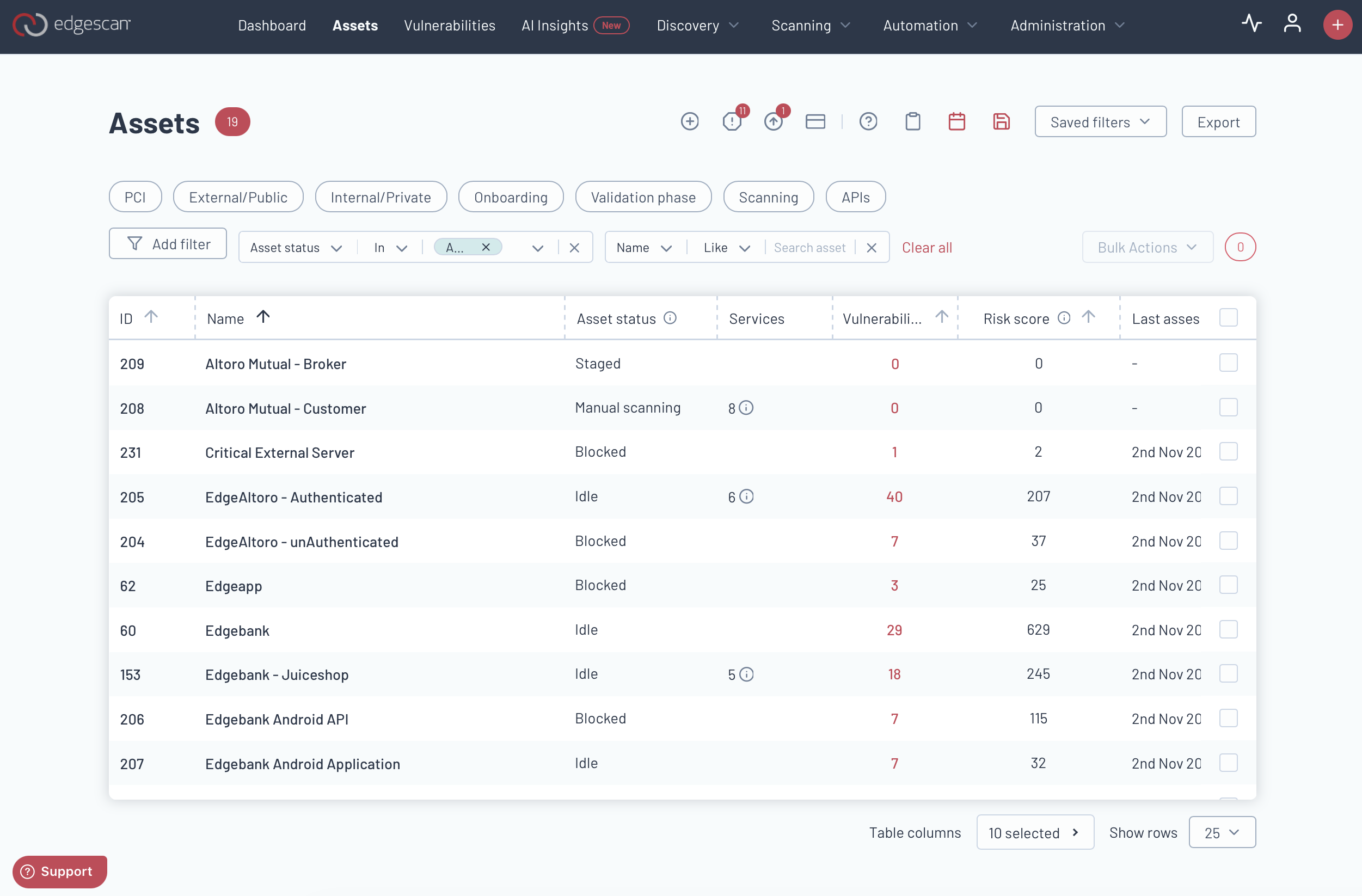
Bulk Actions
The Edgescan Asset Page offers a range of functions such as creating assets, handling asset blockers, checking licenses, and copying API URLs. Users can conveniently schedule exports, save filters, and export data in JSON, XLSX, or CSV formats to effectively manage assets.

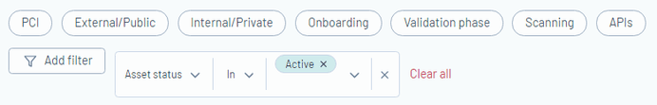
Improved Filtering
Users can take advantage of enhanced filtering options on the Edgescan Asset Page, allowing them to select multiple filters at the same time for easy categorization of assets. These filters include external/public assets, internal/private assets, ongoing scans, and APIs. Users can further refine their search by asset status or name. Additionally, bulk actions are available for adding and deleting tags, exporting data, updating assets, and setting up license auto-renewals.
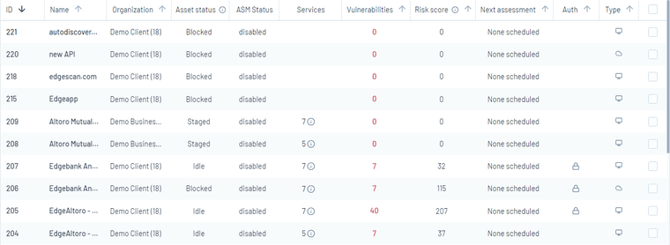
Asset Lists
The Asset Page displays a list that organizes each asset for quick reference and action. Key details for each asset include:
-
ID: A unique identifier for each asset.
-
Organization: The name of the organization to which the asset belongs.
-
Name: The designated name of the asset.
-
Asset Status: Shows whether the asset is active, blocked, or in another state.
-
ASM Status: Indicates if Asset Security Management features are enabled or disabled.
-
Services: The number of services each asset is running.
-
Vulnerabilities: Lists identified security vulnerabilities.
-
Risk Score: A calculated score representing the potential risk posed by the asset.
-
Next Assessment: The scheduled date for the next security assessment.
-
Auth: Whether the asset requires authentication to access.
-
Type: The category of the asset, such as a web app, API, or network.
This structure makes it easy to monitor and manage the cybersecurity health of your assets at a glance.
Assets Details
When accessing an asset on the Edgescan platform, you will be directed to a dedicated page showcasing vital information specific to that asset. This data plays a crucial role in comprehending and maintaining the security of each asset. Located in the top left section of the page, you will find the core details of the asset.

-
Asset Name & Organization: The given name of the asset and the organization it belongs to.
-
Location Specifiers: Includes hostnames, IP addresses, URLs, or CIDR blocks that specify where the asset is located.
-
Scores Section:
-
Priority Score: An assigned value indicating the importance of the asset.
-
Score Calculation: Broken down into application, network, and combined values reflecting the asset's current security assessment.
-
-
Asset Status: Indicates the current condition or operational status of the asset.
-
PCI & ASM Enabled: Shows whether the asset is licensed and enabled for PCI and/or ASM testing.
-
Asset Type: Specifies the nature of the asset, such as 'Network', 'Web Application', or 'API'.
-
Authentication Status: For web applications, shows if the asset has been authenticated or not.
-
Asset Location: Indicates whether the asset is external or internal to the organization.
-
Number of Hosts: The count of network hosts associated with the asset, relevant for network assets.
-
Onboarding Date & Contacts: The date the asset was added to the platform and the points of contact.
To access information on licenses and tags, please refer to the additional details located beneath the displayed screenshot. This organized format ensures a thorough and transparent view of each asset's security status and administrative particulars.
Asset Actions
On each asset's page, you'll find a range of practical actions that make asset management more efficient. You can easily add or modify credentials for secure scanning access, create rules for web application firewalls like Modsecurity, Citrix Netscaler AppFirewall, and F5, and define API locations using swagger files. Furthermore, the capability to export web-crawled data and control scope configurations is crucial for comprehensive analysis.
The "view" button provides convenient access to vulnerabilities and hosts, allowing you to prioritize security actions effectively:
-
Highest Risk Vulnerabilities: Sorts issues by severity, presenting the most critical ones first.
-
Recently Opened Vulnerabilities: Lists newly discovered vulnerabilities, showing the latest entries at the top.
-
Recently Closed Vulnerabilities: Displays vulnerabilities by closure date, with the most recent at the forefront.
-
Oldest Open Vulnerabilities: Orders unresolved vulnerabilities from oldest to newest.
-
Live Hosts: Specific to network assets, it shows all hosts associated with the asset.
Users have the capability to manage asset blockers and delete assets as needed. These comprehensive tools are designed to streamline the process of cybersecurity landscape management, ensuring effectiveness and efficiency.

Risk Over Time
The "Risk Over Time" chart visually illustrates how an asset's risk score fluctuates over time, allowing you to monitor changes and trends in its security posture. The risk score is a comprehensive measure of potential threats, with each vulnerability contributing based on its individual risk rating. Factors considered include the severity of the vulnerability, immediate threat, and its prevalence in the broader security landscape.
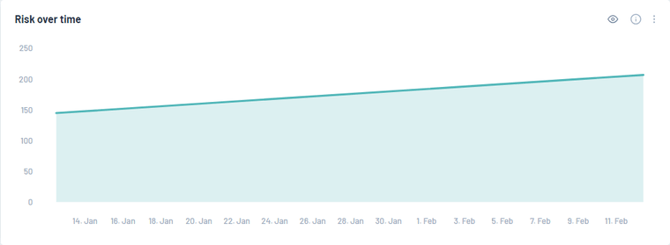
The scoring scale is intentionally weighted to emphasize the impact of more severe vulnerabilities:

This unique scoring system is designed to emphasize the importance of addressing high or critical vulnerabilities, leading to a significant decrease in the overall risk score. By prioritizing these severe risks, the method ensures that a large number of minor vulnerabilities do not disproportionately impact the score, providing a more precise reflection of an asset's actual security status. Monitoring the line graph's upward trend signals a growing risk over time, highlighting the need for thorough inspection and remediation efforts to enhance the asset's defence against potential cyber threats.
Notes
This feature allows you to add notes to an asset, providing important context or reminders for future reference. Edgescan analysts can access these notes to gain a better understanding of your asset's profile. It's important to note that while these notes are crucial for communication, they do not trigger notifications. If you require immediate attention or assistance, we recommend reaching out through our standard support channels.
Scanning Schedule
A crucial component of managing assets is the Scan Scheduler, a powerful tool that provides precise control over the scheduling of security assessments. This feature allows users to initiate new assessments or retest assets after fixes have been implemented. The Freeze Window function is particularly beneficial as it enables users to pause scans during specific time periods, such as peak hours, to prevent any performance disruptions. These paused periods are highlighted in red on the calendar, with detailed information available when hovering over them for exact pause and resume times.
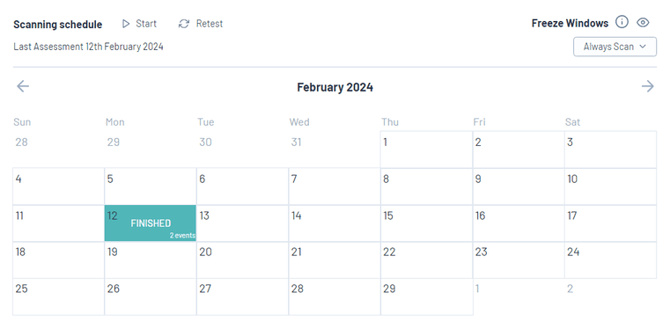
The calendar serves as a comprehensive record of your security activities, with filled dates indicating completed or planned assessments. By clicking on a date, you can access valuable insights such as the assessment's start and finish times, any changes in risk scores, and the identification of newly opened or resolved vulnerabilities. Additionally, you can view the status of hosts that were examined during the assessment. This interactive calendar seamlessly integrates with your operational schedule, ensuring that your security measures are both efficient and seamlessly implemented.
