How To Generate A Report In Edgescan?
The Reporting Module in Edgescan provides a powerful tool for generating comprehensive reports from the platform’s extensive vulnerability data, including Default, PCI, or ASM Reporting capabilities
Version Number: v1.0.2
Published Date: 28 Oct 2025
____________________________________________________________________________
Default Reporting
Default Reporting in Edgescan is designed to be both straightforward and highly customizable, catering to a broad spectrum of reporting needs. Users can choose from three distinct report layouts, each varying in the level of detail provided:
-
Executive Summary: Offers a high-level overview for readers who may not have a technical background.
-
Technical Summary: Presents all identified vulnerabilities with essential details.
-
Technical Detail: Provides an exhaustive analysis of all vulnerabilities, including comprehensive details.
These layouts serve as a foundation upon which users can further tailor their reports, selecting specific sections to include or exclude based on their unique requirements.
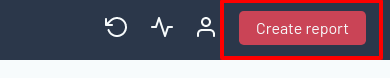
Report Sections
The reports can be divided into various sections to create a customized presentation of data:
- Table of Contents: Gives a clear overview of the report's structure for easy navigation.
- Summary: Provides a concise summary of key findings and insights.
- Delta: Highlights any changes from previous reports.
- 12-Month Vulnerability Overview: Gives an annual perspective on vulnerability trends.
- 3-Month Vulnerability Overview: Focuses on recent vulnerability trends in a quarterly context.
- Asset List: Lists all the assets that were evaluated.
- CIS Controls: Details the adherence to CIS control frameworks.
- Violated SLAs: Identifies any service level agreements that were not met.
- Open Vulnerabilities: Lists all currently unresolved vulnerabilities.
- Closed Vulnerabilities: Lists all currently resolved vulnerabilities.
- False Positives: Lists all false positives recorded in Edgescan for your scoped assets.
- Detail Sections: Includes Definitions, SLA Violations, Request Responses and Consolidated Solutions for a detailed analysis.
Filtering Options
Edgescan's reporting tool allows for precise filtering based on vulnerability risk levels and asset specifications, enabling users to generate reports that closely align with their security posture and asset management strategies:
-
By Risk: Reports can be filtered to include vulnerabilities categorized as Minimal, Low, Medium, High, or Critical.
-
By Asset: Users have the flexibility to report on all assets, all assessed assets, selected assets, or tagged assets, ensuring relevance and specificity.
Reporting Period and Distribution
Users have the flexibility to set the reporting period, spanning from the previous week to the past year, enabling a comprehensive analysis of vulnerabilities over both short and long durations. The reports are conveniently sent via email, with customizable options for scheduling and recurrence to align with the specific needs of the organization.
PCI Reporting
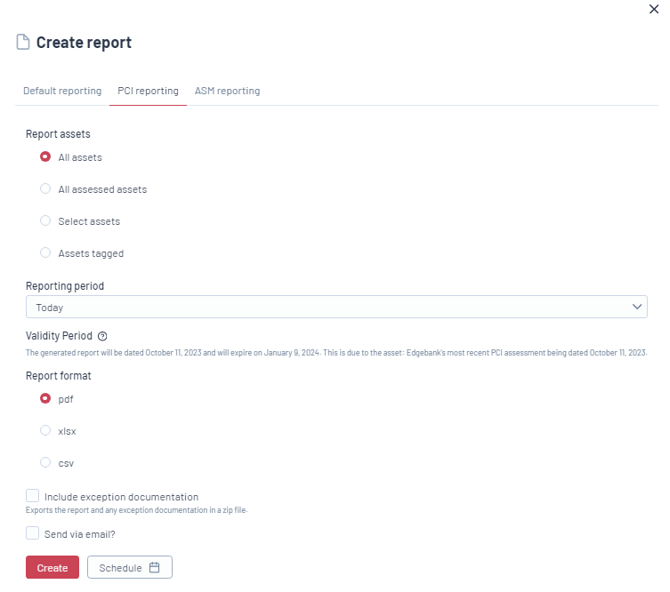
The PCI Reporting feature in Edgescan is specifically designed for PCI customers, ensuring that reports meet PCI compliance requirements. This feature provides flexibility in how assets are reported and the format in which reports are generated, catering to the specific needs of organizations striving for PCI compliance. Key features include:
-
Asset Reporting: You can choose to report on various types of assets, including all assets, all assessed assets, select assets, and tagged assets. This allows for targeted reporting based on your specific needs.
-
Reporting Period: Options include generating a report for today or selecting a custom period. This flexibility ensures you can capture the most relevant data for your PCI compliance efforts.
-
Validity Period: An example of the report's validity is provided, indicating that a report generated on October 11, 2023, would expire on January 9, 2024. This is tied to the date of the latest PCI assessment for the asset, such as "Edgebank's most recent PCI assessment."
-
Report Format: Reports can be generated in PDF, XLSV, or CSV formats, giving you the option to choose the best format for your analysis and record-keeping.
-
Exception Documentation: There's an option to include exception documentation with the report. If selected, the report and any exception documentation will be exported together in a zip file, providing a comprehensive view of compliance and any deviations.
-
Email Distribution and Scheduling: Reports can be sent directly via email, and you can set up a schedule type and recurrence for automatic report generation and distribution. This ensures that stakeholders receive timely updates on PCI compliance status.
Attack Surface Management (ASM) Reporting
ASM Reporting, also known as Attack Surface Management Reporting in Edgescan, is designed to offer valuable insights into your organization's current attack surface. This reporting feature assists in comprehending and overseeing the diverse components that make up your digital footprint, including active and inactive assets, as well as the overall security posture. ASM reports are structured to give a comprehensive overview of your attack surface, broken down into several key sections:
-
Table of Contents: An organized list to help you navigate through the report.
-
Summary: A concise overview of the findings, highlighting critical aspects of your attack surface.
-
Asset List: A detailed inventory of all assets within your scope, providing a clear view of what makes up your digital environment.
-
Live Hosts: Identifies assets that are currently active and accessible, crucial for understanding the live components of your attack surface.
-
Dead Hosts: Lists assets that are inactive or no longer reachable, helping in cleaning up and managing digital assets efficiently.
You have flexibility in how you report on assets, enabling targeted analysis based on your specific needs:
-
All Assets: Generate reports that cover every asset within your environment.
-
Select Assets: Focus on specific assets you choose, allowing for detailed examination of particular areas.
-
Assets Tagged: Utilize tags to report on categorized or grouped assets, aiding in organized analysis.
-
Select Hosts: Narrow down the report to include only certain hosts, providing insights into specific segments of your network.
Reporting Period and Distribution
-
Reporting Period: Choose to generate a report based on data from today or select a custom period to fit your analysis timeframe.
-
Send via Email: An option to directly email the generated report to relevant stakeholders, ensuring timely communication of your attack surface status.
-
Create Schedule: Set up automated reporting schedules to regularly monitor and manage your attack surface. This proactive approach helps in maintaining an up-to-date understanding of your digital environment and its security posture